-
Notifications
You must be signed in to change notification settings - Fork 15
Cryptography, Padding Oracles
Tom Stuart edited this page Sep 7, 2016
·
13 revisions


- A brief history of cryptography
- Herodotus wrote of secret messages written on wood and covered in wax so that they appeared blank and, more outlandishly, writing a message on someone's head and waiting for their hair to regrow, swallowing balls of silk sealed in wax, invisible ink, etc.
- Known as Steganography (steganos = covered, graphein = to write)
- Works quite well but has a fundamental weakness: if the message is discovered, all information is revealed
- So the development of Cryptography (kryptos = hidden), the message is not hidden but its meaning is so it can be intercepted but the information not lost
- Transposition: where the letters retain their identity but change position, e.g. using a device such as a scytale
- Substitution: where the letters retain their position but change their identity, e.g. the Caesar cipher
- To simplify sharing algorithms (e.g. a substitution alphabet), can introduce the idea of a key which helps generate the substitution, e.g. a key word/phrase for the Caesar cipher
-
Symmetric-key encryption (share the same key)
- Attack on substitution cipher if we know the language of the plain text: frequency analysis both of letters and pairs of letters (digrams), trigrams, etc.
-
One-Time Pad

-
XOR message with key of the same length (XOR is addition modulo 2)
- Preserves the randomness completely
- c = m ^ k
- m = c ^ k
- Shannon's "Perfect secrecy"
- Impractical in practice due to key length
- Block ciphers
-
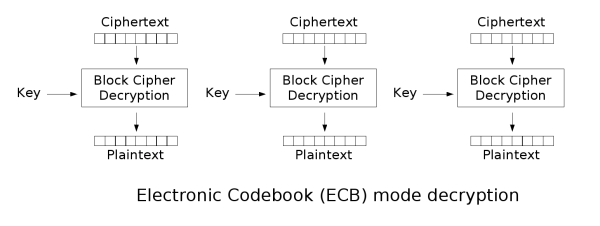
Electronic Codebook
- Padding and PKCS7
- The problem with ECB: the same message produces the same ciphertext
-
Cipher Block Chaining
-
Electronic Codebook
- The Padding Oracle Attack
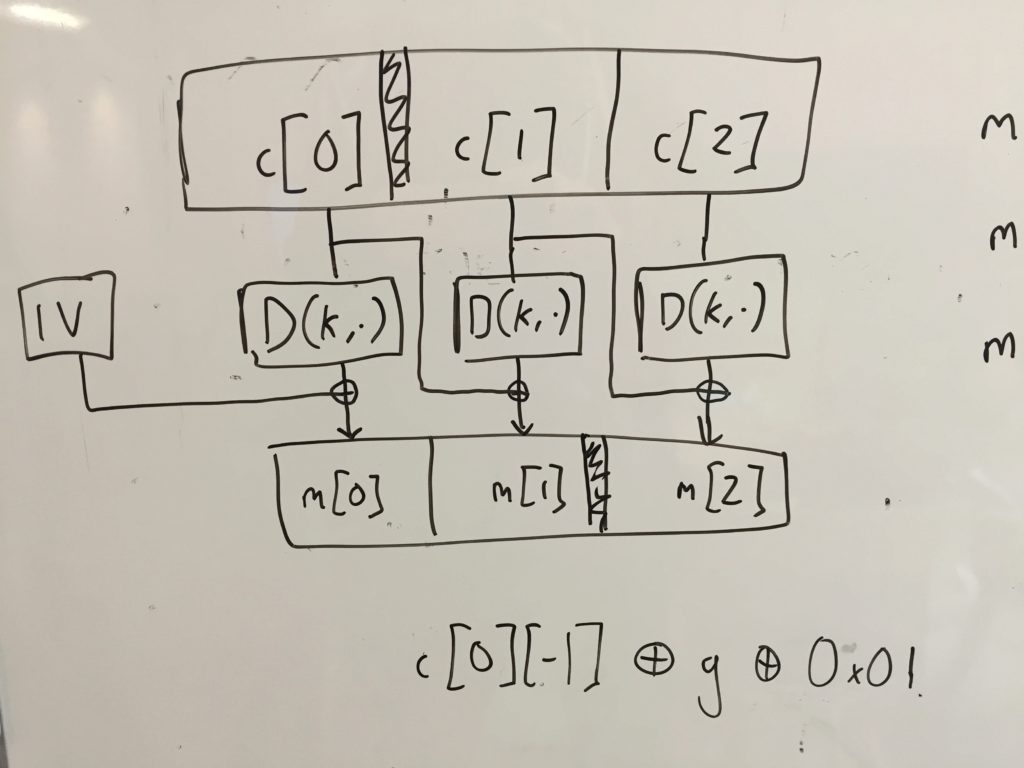


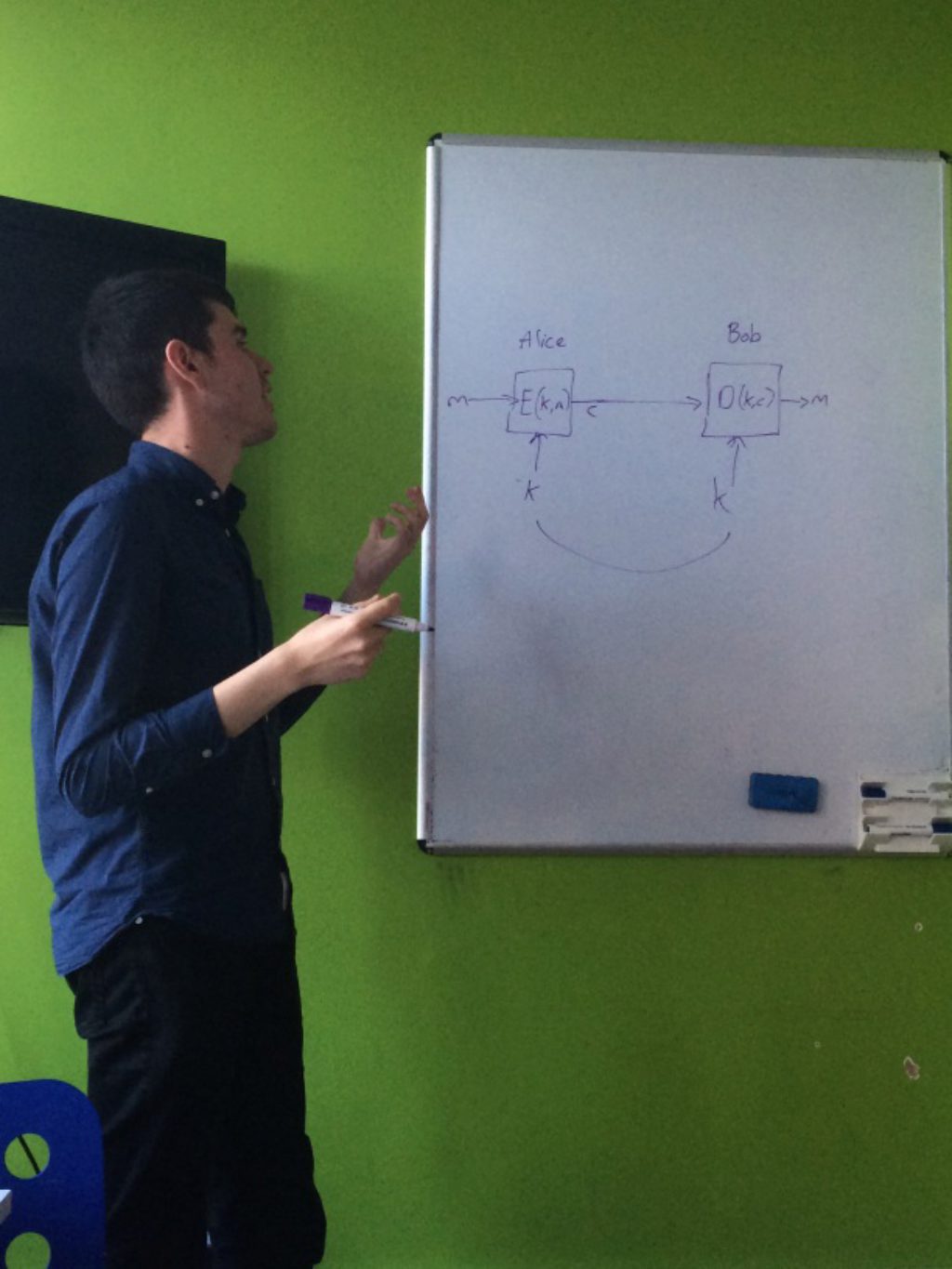
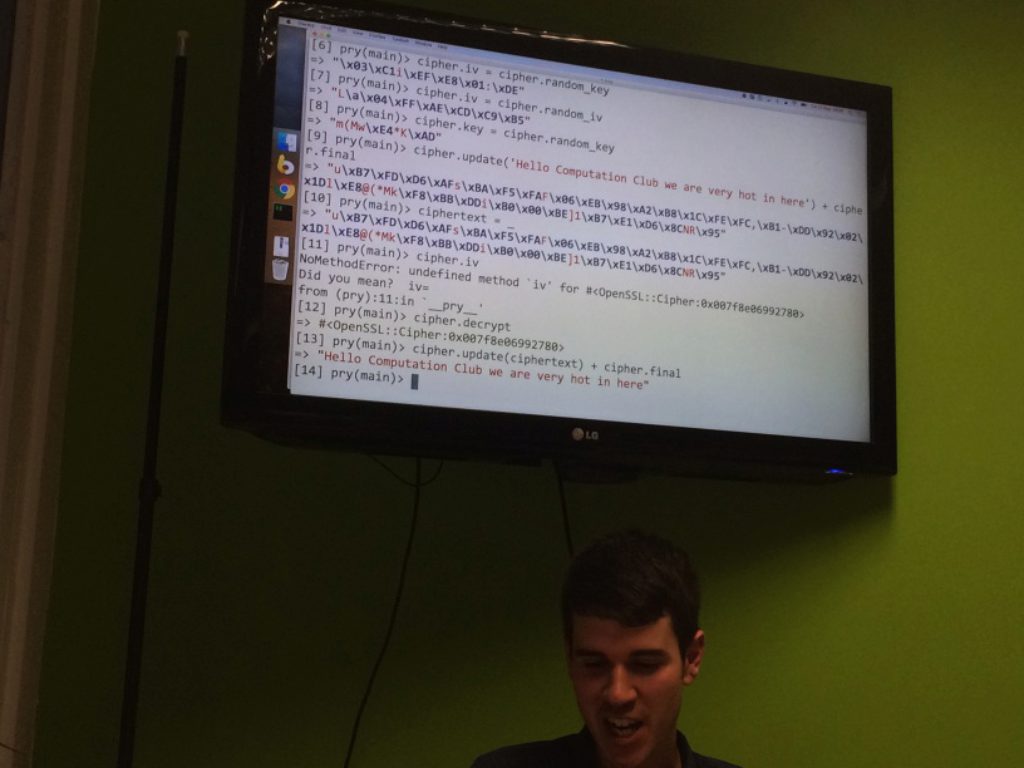
- Review CBC and how encryption and decryption works, concentrating on XOR
- Padding errors
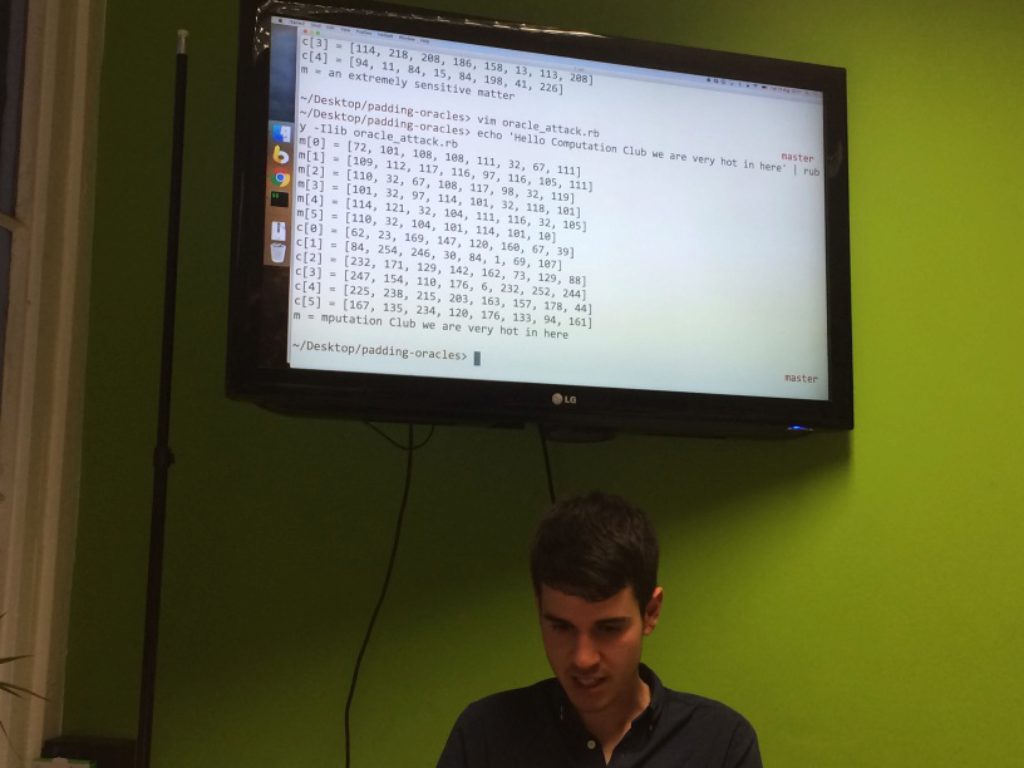
- Guess the last byte of a block by exploiting padding checks
- What if there's no explicit padding error? Side-channel attacks still a possibility
- Real world examples of vulnerabilities
- Simon Singh, "The Code Book"
- Dan Boneh, Stanford University, "Cryptography I"
- Rob Heaton, "The Padding Oracle Attack - why crypto is terrifying"
- Bruce Barnett, "CBC Padding Oracle Attacks Simplified – Key concepts and pitfalls"
- An implementation of the padding oracle attack capable of decrypting a ciphertext encoded with DES and AES with cipher block chaining in Ruby:
padding-oracles
- Home
- Documentation
- Choosing a Topic
- Shows & Tells
- Miscellaneous
- Opt Art
- Reinforcement Learning: An Introduction
- 10 Technical Papers Every Programmer Should Read (At Least Twice)
- 7 More Languages in 7 Weeks
- Lua, Day 1: The Call to Adventure
- Lua, Day 2: Tables All the Way Down
- Lua, Day 3
- Factor, Day 1: Stack On, Stack Off
- Factor, Day 2: Painting the Fence
- Factor, Day 3: Balancing on a Boat
- Elm, Day 1: Handling the Basics
- Elm, Day 2: The Elm Architecture
- Elm, Day 3: The Elm Architecture
- Elixir, Day 1: Laying a Great Foundation
- Elixir, Day 2: Controlling Mutations
- Elixir, Day 3: Spawning and Respawning
- Julia, Day 1: Resistance Is Futile
- Julia, Day 2: Getting Assimilated
- Julia, Day 3: Become One With Julia
- Minikanren, Days 1-3
- Minikanren, Einstein's Puzzle
- Idris Days 1-2
- Types and Programming Languages
- Chapter 1: Introduction
- Chapter 2: Mathematical Preliminaries
- Chapter 3: Untyped Arithmetic Expressions
- Chapter 4: An ML Implementation of Arithmetic Expressions
- Chapter 5: The Untyped Lambda-Calculus
- Chapters 6 & 7: De Bruijn Indices and an ML Implementation of the Lambda-Calculus
- Chapter 8: Typed Arithmetic Expressions
- Chapter 9: The Simply-Typed Lambda Calculus
- Chapter 10: An ML Implementation of Simple Types
- Chapter 11: Simple Extensions
- Chapter 11 Redux: Simple Extensions
- Chapter 13: References
- Chapter 14: Exceptions
- Chapter 15: Subtyping – Part 1
- Chapter 15: Subtyping – Part 2
- Chapter 16: The Metatheory of Subtyping
- Chapter 16: Implementation
- Chapter 18: Case Study: Imperative Objects
- Chapter 19: Case Study: Featherweight Java
- The New Turing Omnibus
- Errata
- Chapter 11: Search Trees
- Chapter 8: Random Numbers
- Chapter 35: Sequential Sorting
- Chapter 58: Predicate Calculus
- Chapter 27: Perceptrons
- Chapter 9: Mathematical Research
- Chapter 16: Genetic Algorithms
- Chapter 37: Public Key Cryptography
- Chapter 6: Game Trees
- Chapter 5: Gödel's Theorem
- Chapter 34: Satisfiability (also featuring: Sentient)
- Chapter 44: Cellular Automata
- Chapter 47: Storing Images
- Chapter 12: Error-Correcting Codes
- Chapter 32: The Fast Fourier Transform
- Chapter 36: Neural Networks That Learn
- Chapter 41: NP-Completeness
- Chapter 55: Iteration and Recursion
- Chapter 19: Computer Vision
- Chapter 61: Searching Strings
- Chapter 66: Church's Thesis
- Chapter 52: Text Compression
- Chapter 22: Minimum spanning tree
- Chapter 64: Logic Programming
- Chapter 60: Computer Viruses
- Show & Tell
- Elements of Computing Systems
- Archived pages