-
Notifications
You must be signed in to change notification settings - Fork 88
PSK
Use of PSKs provides post-quantum security and is recommended in cases where the users know and trust each other and where they can meet to exchange the keys. PSKs should never be exchanged with strangers or contacts who might be malicious.
The TFC accounts should be exchanged using some authenticated channel. An authenticated (and preferably confidential) channel such as an end-to-end encrypted Signal-call should also be used to agree on the date and location for exchanging the PSK file.
The TFC account can also be exchanged in a separate, initial, in-person meeting which allows hiding the TFC account from potential eavesdroppers of the authenticated channel.
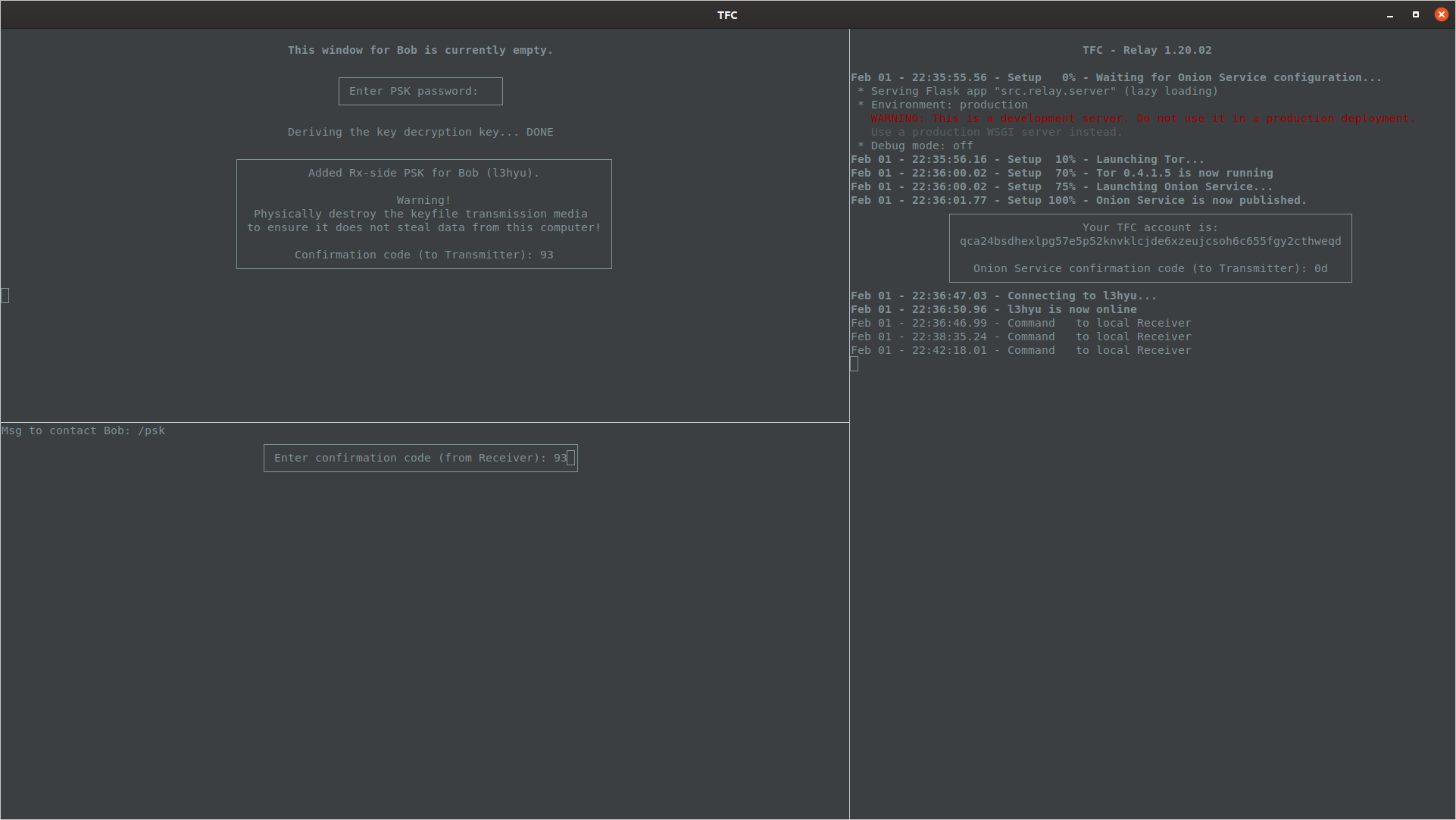
Enter the contact's TFC account, nick and select PSK as the key exchange method.
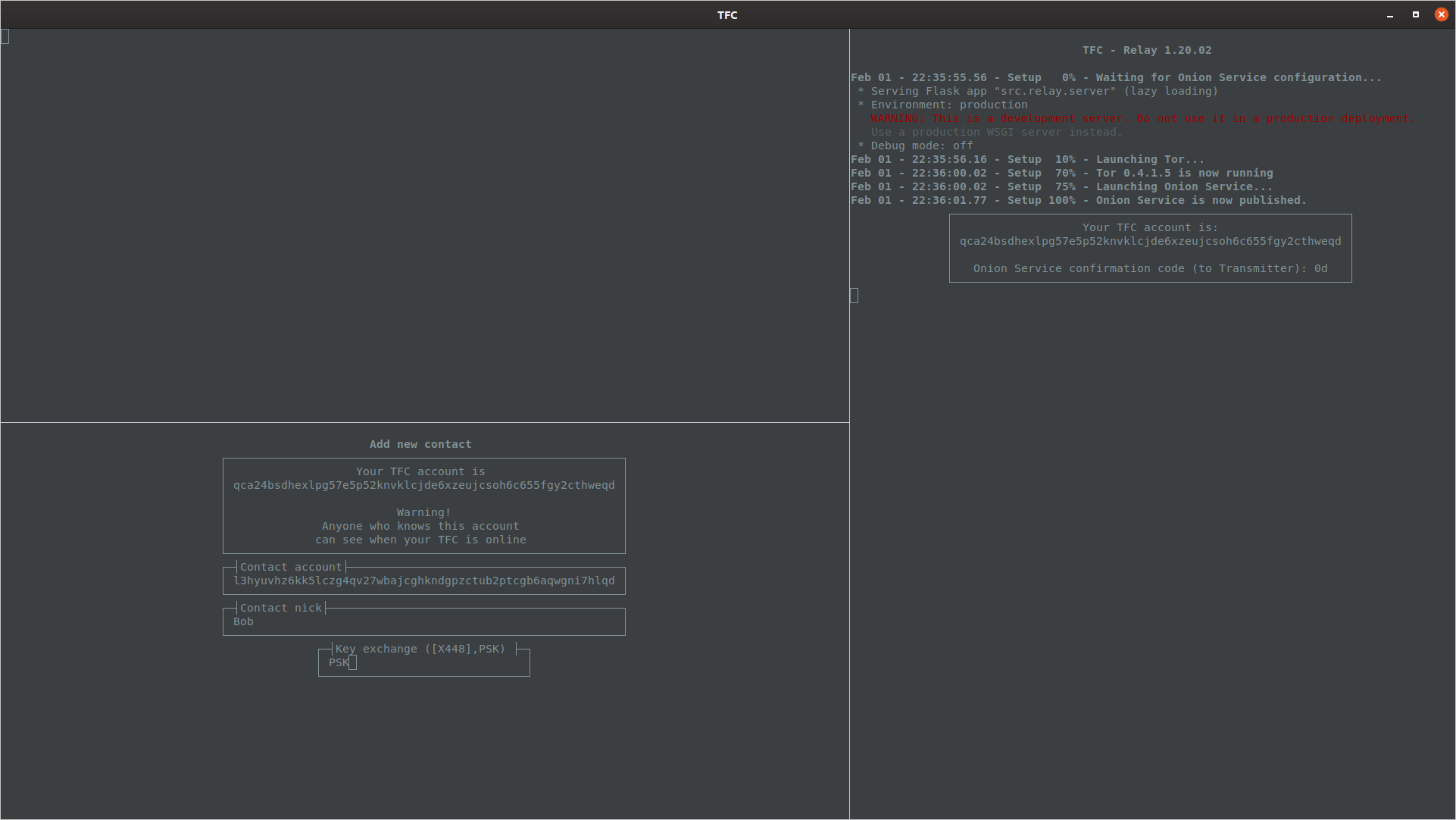
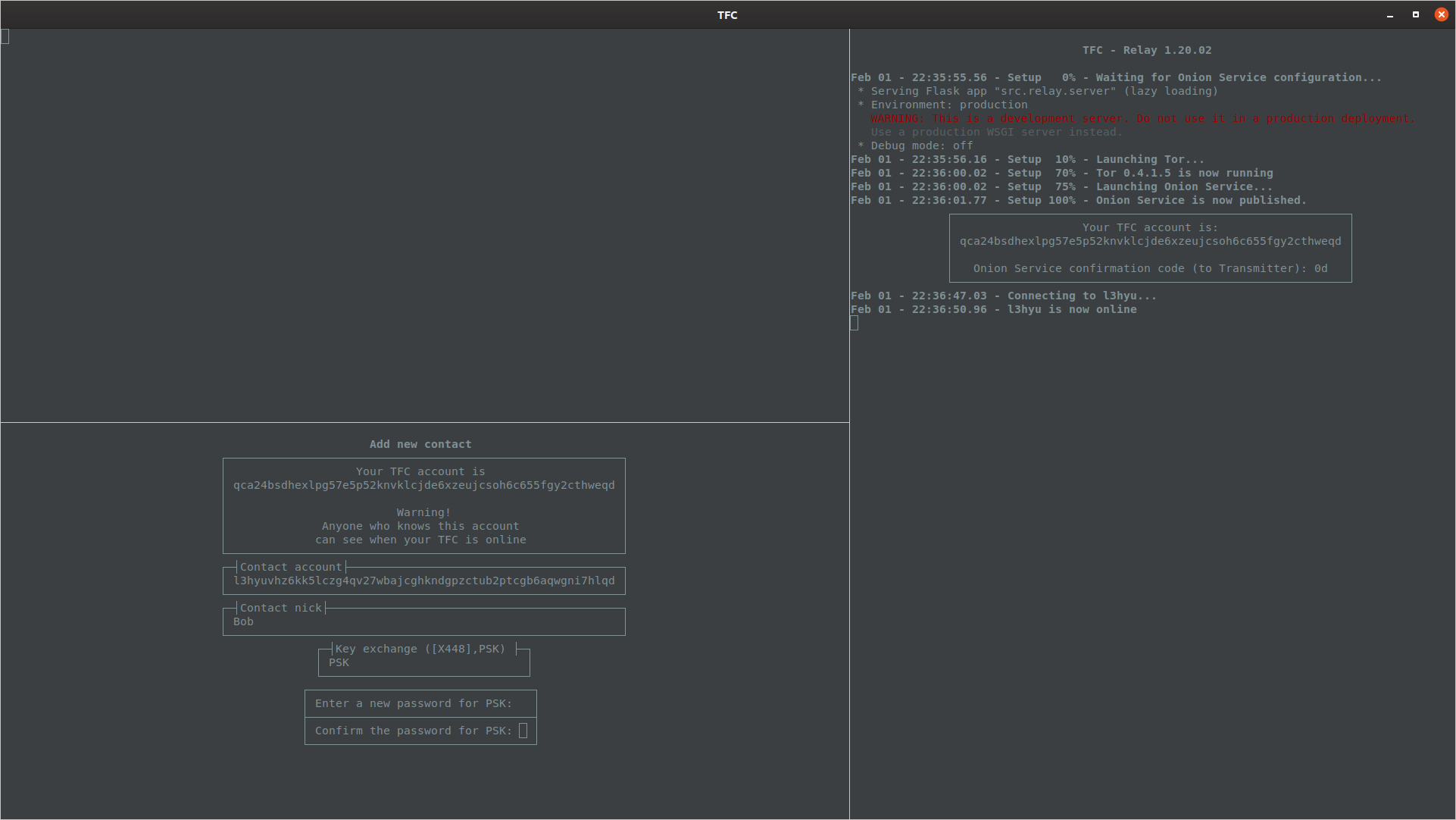
PSK needs to be protected during transit, so Transmitter Program prompts the user to enter and confirm a password that needs to be delivered to the contact through some secret channel (e.g., during/after key exchange meeting).
The password should be strong to ensure an attacker who manages to make a copy of the encrypted PSK cannot decrypt it.
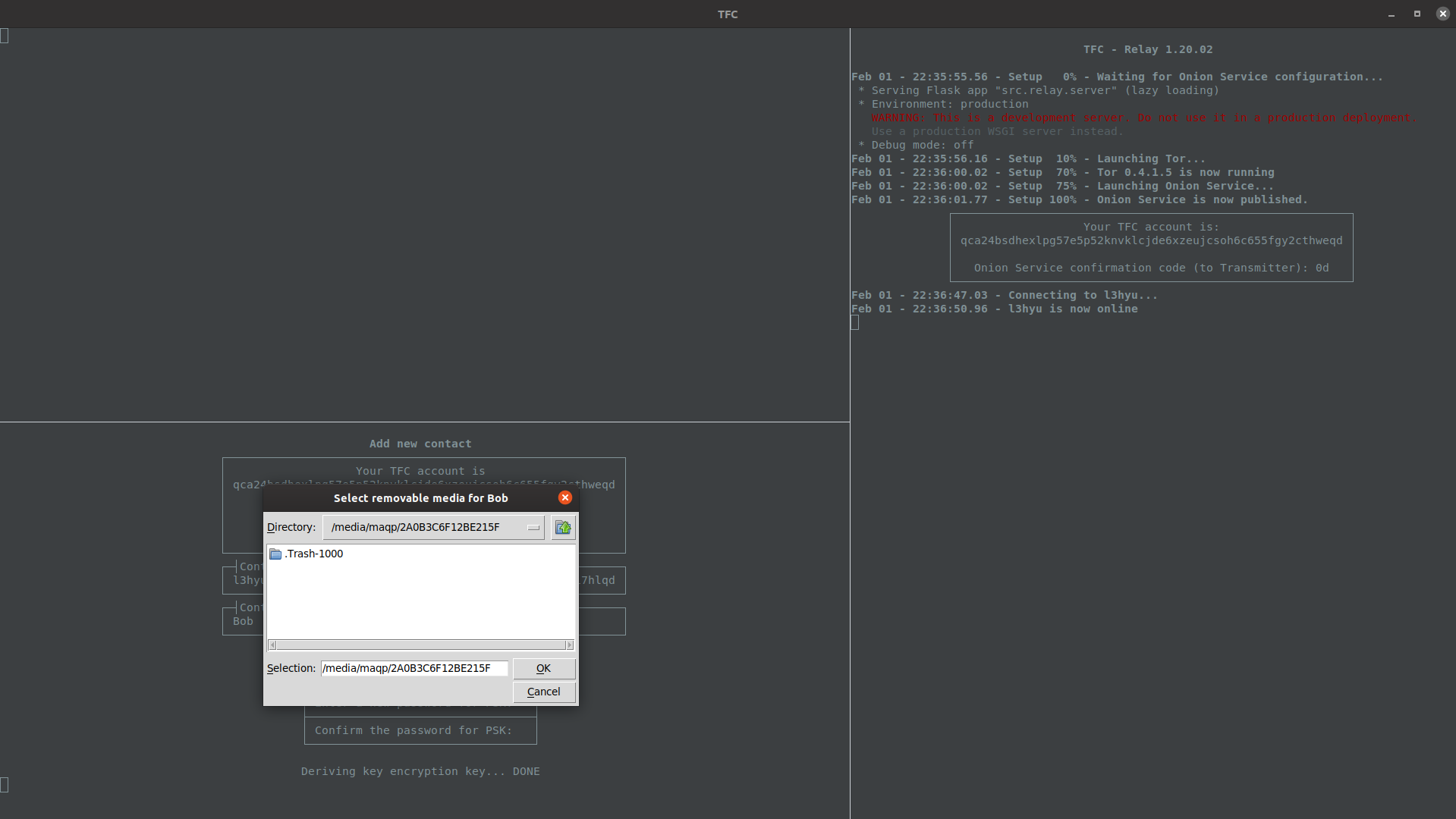
Next, the user must select the directory for removable media to store the PSK in. For this step, the user needs a removable media that is inserted into their Source Computer's USB slot. To protect the user, this removable media must come from a sealed packaging. The user must then choose the removable media as the directory for the PSK in the GUI prompt.
The Transmitter Program will then export a copy of the keys to the Receiver Program on destination Computer. Enter the confirmation code for the keys.
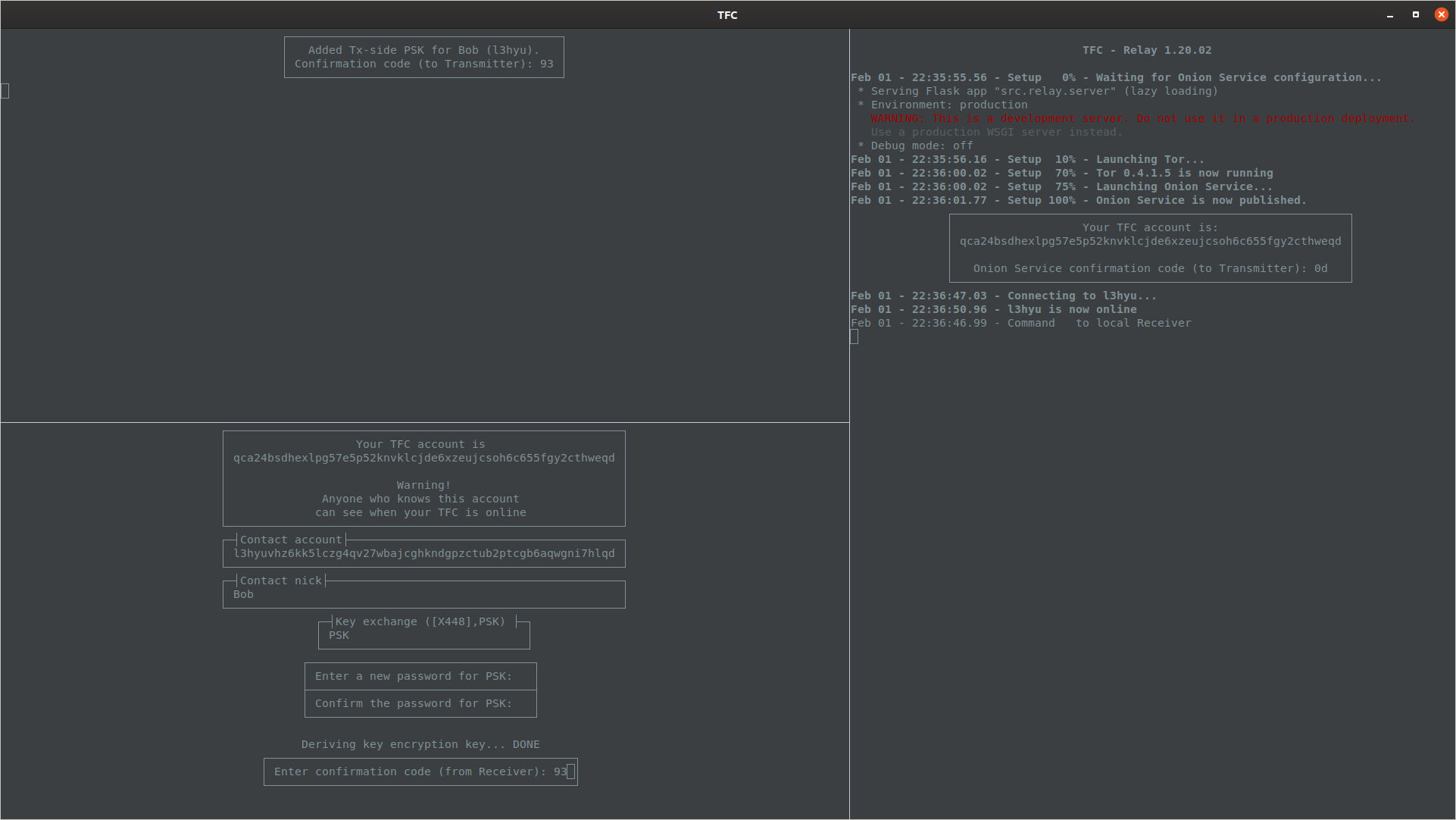
At this point of the key exchange the Transmitter Program's contact list displays a (No contact key) message next to the key exchange method. This tells the user they have not yet imported the PSK from contact that allows the user to decrypt incoming messages. The next step is to physically exchange the keys.
The users must then meet in person, and exchange the PSK transmission media. During transport extreme care must be taken to ensure no adversary gains access to the PSK transmission media.
After the meeting, the user must insert the removable media of the contact to their Destination Computer (the one that runs Receiver Program).
WARNING! If the user accidentally connects the contact's PSK transmission media to their Source Computer instead of their Destination Computer, all security of their TFC endpoint should be assumed to have been lost permanently.
WARNING! If the PSK transmission media contains e.g. a covert transmitter, it might covertly broadcast sensitive data from Destination Computer in real time.
The user should never exchange PSKs with contacts they don't personally know and trust, but instead use X448. Trust but verify is a good strategy, so to mitigate this threat, some help may result from wrapping the PSK transmission media carefully e.g. in aluminum foil to create a Faraday cage that could attenuate the covert transmission signal enough until the device is disconnected and physically destroyed. For larger institutions making use of TFC with PSKs, a Faraday cage glove box (i.e. an EMI test enclosure) reduces the chance of leakage and significantly simplifies the workflow if multiple PSKs need to be imported.
To import the PSK, the user must first select the contact, and then enter the command /psk to their Transmitter Program. The command will open a file selection prompt on Receiver Program. They must select the protected PSK file from the contacts transmission media.
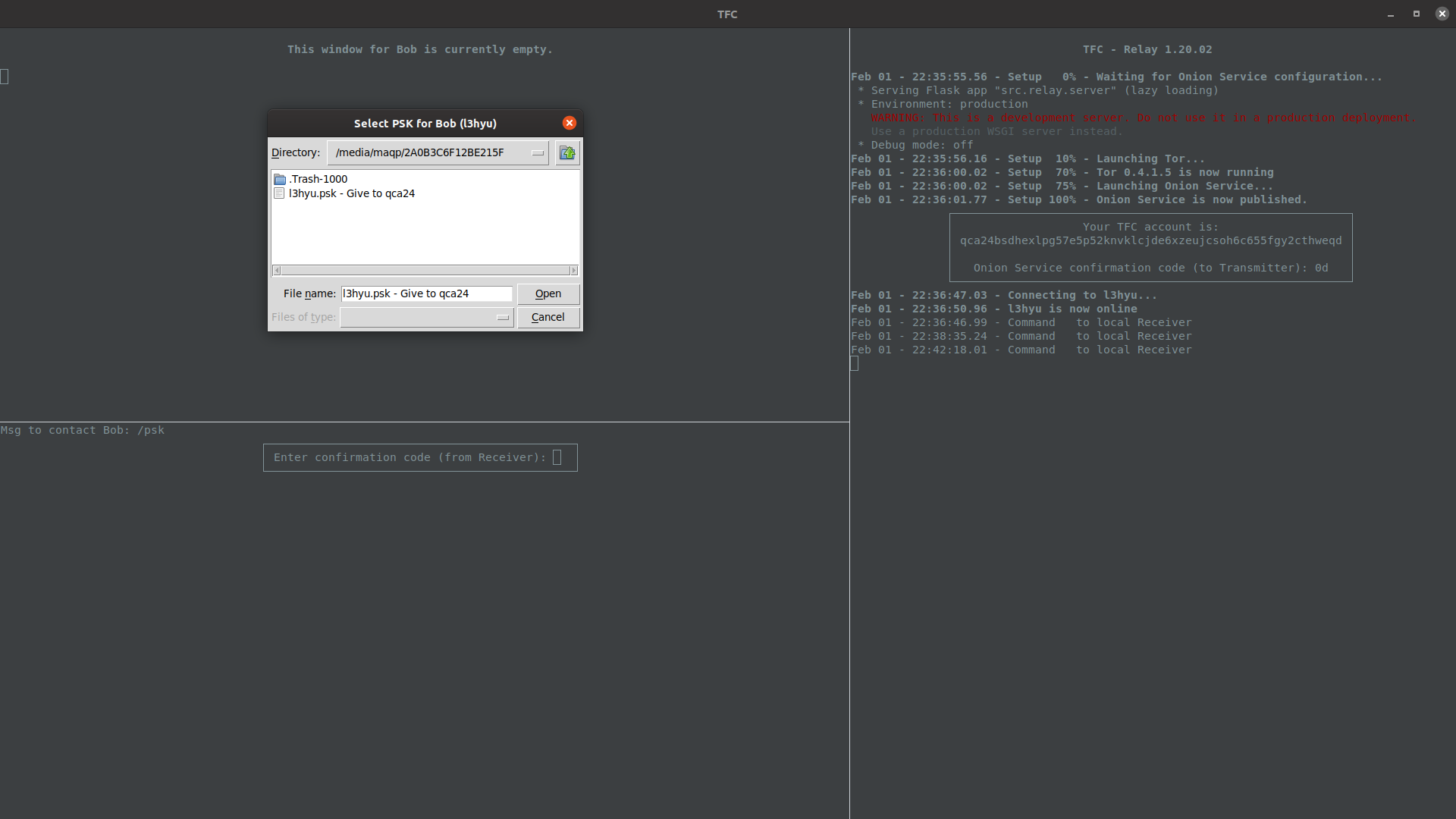
The user must then enter the password given to them by their contact to decrypt the contact's PSK.
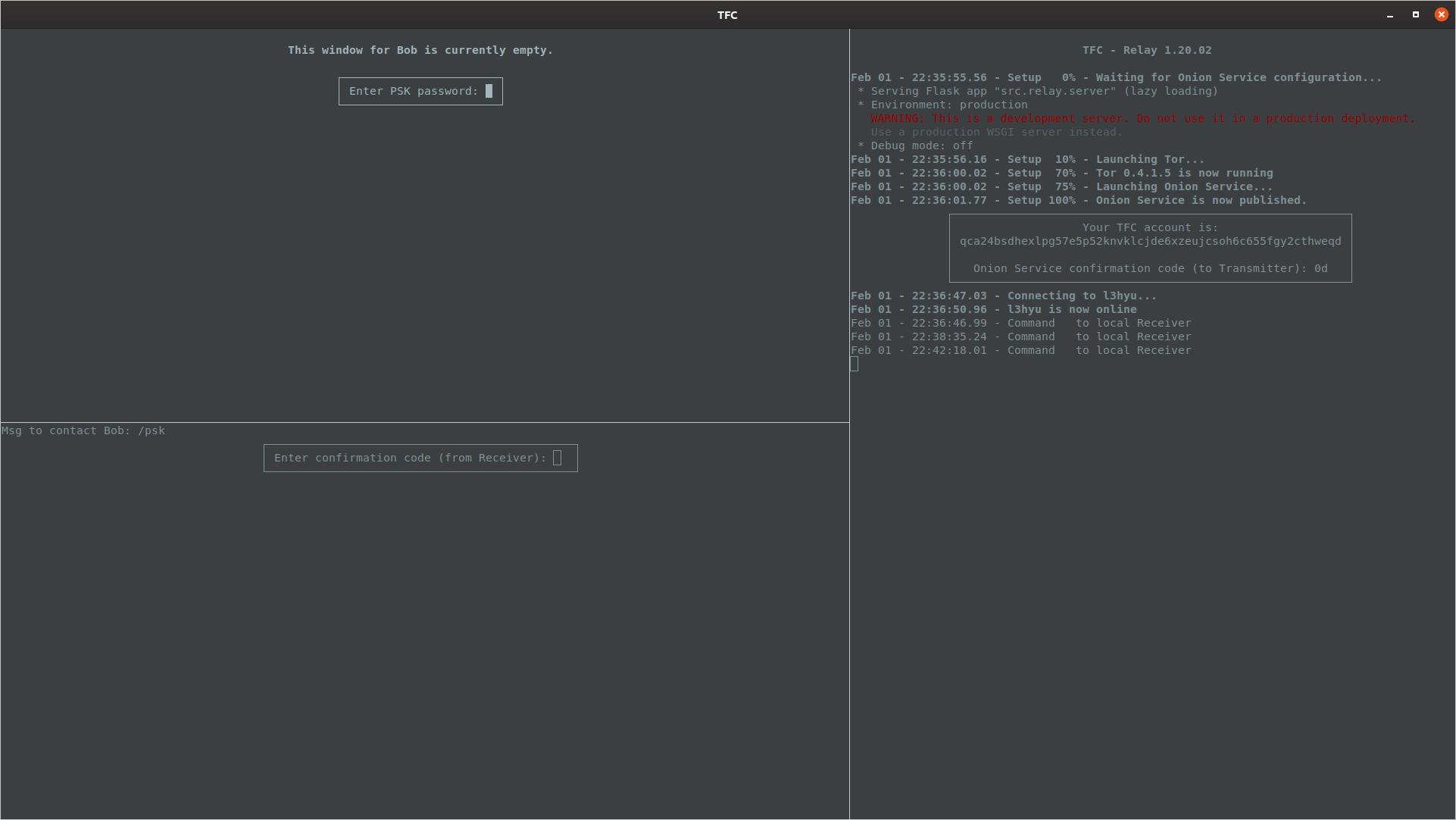
Once Receiver Program has decrypted the PSK file, it will copy the keys to its key database and overwrite the encrypted PSK file. The Receiver Program will then display the user a confirmation code that must be written to the Transmitter Program's prompt.
This code verifies the user has indeed imported the PSK, so the Transmitter Program knows to remove the trailing (No contact key) label from the key exchange type (PSK), shown when the user views contact details with the /names command.
The key exchange is now complete, but there's one more thing to do:
Always assume the PSK transmission media received from contact steals sensitive data from Destination Computer. Never give the media back to the contact. It is the responsibility of the contact to know they cannot have their device back. As the Receiver Program's warning instructs, destroy the transmission media to ensure no data escapes the Destination Computer.
Receiver Program overwrites the PSK file on the removable device after keys have been imported. This is however not a strong guarantee. Would an adversary succeed in recovering the PSK file and guessing the password, they could decrypt all messages trivially, as the PSK is the root key from which the forward secret keys are generated.
To guarantee such attacks do not happen, physically destroy the removable media by hammering/drilling/angle grinding the memory chips, The Guardian style.