For the lastest installation instructions for this repo please see this blog post: IR TALES: THE QUEST FOR THE HOLY SIEM: GRAYLOG + AUDITD + OSQUERY
WARNING
This Ansible playbook will allocate half of the systems memory to Elasticsearch. For example, if a machine has 16GBs of memory, 8GBs of memory will be allocated to Elasticsearch.
WARNING
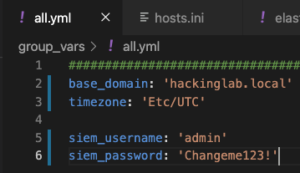
vim macos-workshop/ChooseYourSIEMAdventure/hosts.iniand add the Graylog server IP address under[graylog]vim macos-workshop/ChooseYourSIEMAdventure/group_vars/all.ymland set:base_domain–<external_domain - group_vars/all.yml>timezone– OPTIONAL – The default timezone is UTC+0siem_username– Ignore this settingsiem_password– Set the Graylog admin passwordvim macos-workshop/ChooseYourSIEMAdventure/group_vars/graylog.ymland set:hostname– Set the desired hostname for the servergraylog_version– Set the desired version of Graylog to usebeats_port– OPTIONAL – Set the port to ingest logs using BEAT clientselastic_version– OPTIONAL – Set the desired version of Elasticsearch to use with Graylog – best to leave as defaultmongo_version– OPTIONAL – Set the desired version of Mongo to use with Graylog – best to leave as defaultmongo_admin_username– OPTIONAL – Set Mongo admin username – best to leave as defaultmongo_admin_password– Set the Mongo admin user passwordmongo_graylog_username– Set Mongo username for Graylog usermongo_graylog_password– Set Mongo password for Graylog user
- SSH into Elastic EC2 instance
sudo suapt install certbot python3-certbot-nginx -ycertbot --nginx -d graylog.<external domain>- Enter the e-mail for the admin of the domain
- Enter
Afor Terms of Service - Enter
Nto share e-mail with EFF - Enter
2to redirect HTTP traffic to HTTPS - Review NGINX config:
/etc/nginx/conf.d/graylog.conf systemctl restart nginx
- Open browser to
https://graylog.<external domain>and login - Enter
adminfor username - Enter
<siem_password>into Password - System > Users and Teams
- Select "Create User" in top right
- Enter
threathunterinto username - Enter
threathunterinto full name - Leave e-mail blank
- Enter
6for user session timeout - Enter a password for the user
- Select
User inspectorfor roles 
- Select "Create user"
- System > Indicies
- Select "Create index set" in the top right
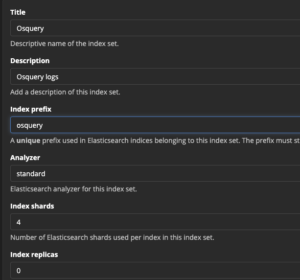
- Enter
Osqueryfor name - Enter
Osquery logsfor description - Enter
osqueryfor index prefix - Leave everything as default
- Select "Save"
- Repeat the steps above to create an index called "test" and "sysmon
- Select "Streams" at the top
- Select "Create stream" in the top right
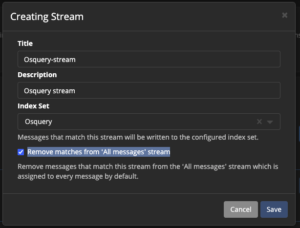
- Enter
Osquery-streamfor name - Enter
Osquery streamfor description - Select "Osquery" for index set
- Check "Remove matches from 'All messages' stream"
- Select "Save"
- Repeat the steps above to create an index called "test"
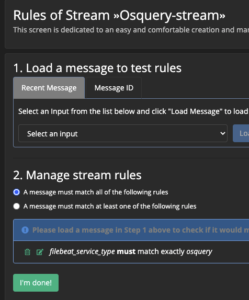
- Select "Manage Rules" for Osquery stream
- Select “Add stream rule” on the right
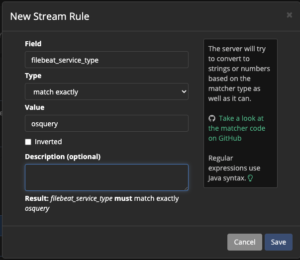
- Enter
event_modulefor field - Select
match exactlyfor type - Enter
osqueryfor value - Select "Save"
- Select "I’m done" in bottom left
- Select "Start stream" for Osquery stream
- Repeat the steps above for test
- System > Inputs
- Select "Raw/Plaintext Kafka" from Input drop down
- Select "Launch new input"
- Enter
Kafka inputinto Title - UNcheck
Legacy Mode - Enter
172.16.50.10:9092into Bootstrap servers - Enter
127.0.0.1:2181into Zookeeper address - Enter
osqueryinto topic filter regex 
- Select "Save"
- Repeat the steps above to create an index called "test" and "sysmon